Work2you has been doing free blogs for a long time, and we insist on helping more people improve their skills. Latest updates
Microsoft PRO 70-686 exam dumps and 70-686 pdf download online, 100% free, practical and effective,
we free update part 70-686 Exam practice, if you want to pass the 70-686 exam certificate,
please select the full version: https://www.pass4itsure.com/70-686.html (VCE + PDF q&as:184 Latest Update)
[PDF] Free Microsoft PRO 70-686 dumps download from Google Drive: https://drive.google.com/open?id=1AnRkEHVsAqaY174JMIe0kqBCLo-R6A3-
[PDF] Free Full Microsoft dumps download from Google Drive: https://drive.google.com/open?id=1gdQrKIsiLyDEsZ24FxsyukNPYmpSUDDO
Exam 70-686: Windows 7, Enterprise Desktop Administrator: https://www.microsoft.com/en-us/learning/exam-70-686.aspx
Who should take this exam?
Candidates for this exam should have a minimum of three years of experience installing, configuring, and administering clients in
a Windows networked environment and also have experience deploying operating systems and applications. Candidates should be
familiar with the client administration capabilities of Windows Server and with management tools such as the System Center suite of products.
Pass4itsure offers the latest Microsoft PRO 70-686 practice test free of charge (42Q&As)
QUESTION 1
A company has an Active Directory Domain Services (AD DS) forest with a single domain.
Domain controllers are located in the companys offices in New York and Boston.
You deploy a group policy at the domain level that includes security filtering.
You discover that Group Policy object (GPO) settings are being applied to computers in the New York office, but not to computers in the Boston office.
You suspect there might be replication problems with the policies. What should you do?
A. Run a Group Policy Results report against computers in the Boston office.
B. Run a Group Policy Modeling report against computers in the Boston office.
C. Use the GpoTool.exe command-line tool.
D. Use the RepAdmin.exe command-line tool.
Correct Answer: A
Explanation
QUESTION 2
Your companys network has client computers that run Windows 7.
A software vendor releases version 2 of an application that your company uses.
Your company currently uses version 1. Version 1 and version 2 are not compatible.
You plan to deploy version 2 of the application.
You have the following requirements:
You need to plan a software deployment process that meets the requirements. What should you do? (Choose all that apply.)
A. Deploy version 2 of the application by using Microsoft Application Virtualization (App-V).
B. Deploy version 2 of the application by using Microsoft Enterprise Desktop (MED-V).
C. Deploy version 2 of the application as a Remote Desktop Services RemoteApp.
D. Deploy version 2 of the application by using a Microsoft System Center Configuration Manager package.
Correct Answer: AB
Explanation
Explanation/Reference:
Microsoft Application Virtualization (MS App-V) platform allows applications to be deployed in real-time to any client from a virtual application server. It removes the need for local installation of the applications. Instead, only the App-v client
needs to be installed on the client machines. All application data is permanently stored on the virtual application server. Whichever software is needed is either streamed or locally cached from the application server on demand and run locally.
The App-V stack sandboxes the execution environment so that the application does not make changes to the client itself (OS File System and/or Registry). App-V applications are also sandboxed from each other, so that different versions of
the same application can be run under
App-V concurrently.
http://en.wikipedia.org/wiki/Microsoft_App-V
QUESTION 3
A company uses Microsoft Deployment Toolkit (MDT) 2010 to deploy Windows 7 Enterprise and Microsoft Office 2010. The company is replacing existing computers with new 64-bit computers.
You have the following requirements:
You need to create an image that meets these requirements.
What should you do? (Choose all that apply.)
A. Import the Windows 7 Enterprise x86 source files.
B. From the MDT deployment workbench, select the Custom Task Sequence template.
C. Use a reference computer and capture a WIM image.
D. From the MDT deployment workbench, select the Sysprep and Capture template.
E. Import the necessary OEM drivers.
F. Import the 32-bit version of Office 2010.
G. Import the 64-bit version of Office 2010.
H. Import the Windows 7 Enterprise x64 source files.
Correct Answer: ABEF
Explanation
Explanation/Reference:
hints:
The specialized hardware is compatible with Windows 7 but only 32-bit drivers are available from the manufacturer.
QUESTION 4
Your company’s network includes a main office and several branch offices. The branch offices are connected to the main office by high-latency links. All client computers run Windows 7 Enterprise, and all servers run Windows Server 2008
R2. Servers are located in each of the branch offices.
Client computers in the branch offices frequently access a specific group of files on a file server named Server1. These access requests consume significant amounts of bandwidth and reduce the speed of higher-priority traffic.
You need to reduce the bandwidth that is consumed by requests for frequently accessed files.
What should you do?
A. Configure BranchCache in Hosted Cache mode on client computers in the main office and the branch offices.
B. Configure BranchCache in Distributed Cache mode on client computers in the main office and the branch offices.
C. Enable the BranchCache For Network Files role service on Server1. Configure BranchCache in Distributed Cache mode on a server computer in only the branch offices.
D. Enable the BranchCache For Network Files role service on Server1. Configure BranchCache in Hosted Cache mode on a server computer in only the branch offices.
Correct Answer: C
Explanation
Explanation/Reference:
BranchCacheTM is designed to reduce WAN link utilization and improve application responsiveness for branch office workers who access content from servers in remote locations. Branch office client computers use a locally maintained
cache of data to reduce traffic over a WAN link. The cache can be distributed across client computers (Distributed Cache mode) or can be housed on a server in the branch (Hosted Cache mode).
Distributed Cache mode
If client computers are configured to use Distributed Cache mode, the cached content is distributed among client computers on the branch office network. No infrastructure or services are required in the branch office beyond client computers
running Windows 7.
Hosted Cache mode
In hosted cache mode, cached content is maintained on a computer running Windows Server 2008 R2 on the branch office network.
hints: no server are located in the branch office. http://technet.microsoft.com/en-us/library/dd637832(v=ws.10).aspx
QUESTION 5
A Windows Server 2008 R2 server named SERVER01 has the Windows Deployment Services (WDS) role installed. SERVER02 is running DHCP services. You prestage computer objects in Active Directory. You plan to use WDS to deploy
Windows 7 to the prestaged computers. When you try to deploy an image by using PXE, the process fails. You need to ensure that SERVER01 responds to prestaged client computers only. From WDS, what should you do? (Choose all that
apply.)
A. On the DHCP tab, select Configure DHCP option 60 to indicate that this server is also a PXE server.
B. On the Advanced tab, select Authorize this Windows Deployment Services server in DHCP.
C. On the PXE Response tab, select Respond to all client computers (known and unknown).
D. On the DHCP tab, select Do not listen on Port 67.
E. On the PXE Response tab, select Respond only to known client computers.
F. On the Advanced tab, select Do not authorize this Windows Deployment Services server in DHCP.
Correct Answer: BE
Explanation
Explanation/Reference:
hints: prestaged computers = known client computers
QUESTION 6
Your company has a custom Web application that uses a self-signed SSL certificate. The company has an internal certification authority (CA) and uses autoenrollment. When external users attempt to start the Web application, Internet
Explorer displays an error message that recommends closing the Web page rather than continuing to the application. You need to ensure that Internet Explorer does not display the error message. What should you do?
A. Install the current certificate into the personal store on each client computer. Add the applications URL to the Trusted Sites zone in Internet Explorer.
B. Install the current certificate into the computer store on each client computer.
C. Purchase and install a commercial certificate on the CA server. Ensure that users trust the issuing CA.D. Issue a root certificate from the internal CA on the external users computers.
Correct Answer: B
Explanation
QUESTION 7
Your companys network is shown in the following diagram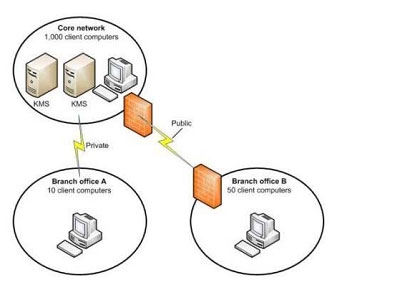
There is a VPN between Branch Officebranch office B and the Core Networkcore network.
The company plans to deploy Windows 7 to all client computers.
You need to manage the deployment to ensure that client computers in branch office A and in branch office B can activate Windows.
What should you do? (Each correct answer presents part of the solution. Choose all that apply.)
A. Configure DNS so that client computers in branch office A use the Key Management Service (KMS) in the core network.
B. Deploy the Key Management Service (KMS) in branch office B.
C. Deploy the Key Management Service (KMS) in branch office A.
D. Configure DNS so that client computers in branch office B use the Key Management Service (KMS) in the core network.
Correct Answer: AB
Explanation
QUESTION 8
You are deploying an App-V client application to the New York office.
You need to ensure that the application will be installed at a specific time.
What should you use to deploy the application?
A. ConfigMgr
B. a Group Policy object (GPO) with a software installation policy.
C. MED-V
D. Microsoft Deployment Toolkit
Correct Answer: A
Explanation
QUESTION 9
Your company has client computers that run Windows 7 Enterprise.
Each computer in the company is required to boot into a different Windows 7 application environment without compromising the main Windows 7 Enterprise installation.
You need to create a new Native Boot VHD that will host the alternate Windows 7 environments.
Which command should you use?
A. BCDEdit.exe
B. Bootcfg.exe
C. DiskPart.exe
D. BCDboot.exe
Correct Answer: D
Explanation
Explanation/Reference:
http://www.techexams.net/forums/windows-7-exams/66547-bcdedit-bcdboot- difference.html
BCDboot is a tool used to quickly set up a system partition, or to repair the boot environment located on the system partition. The system partition is set up by copying a small set of boot environment files from an installed Windows?image.
BCDboot also creates a Boot Configuration Data (BCD) store on the system partition with a new boot entry that enables you to boot to the installed Windows image. BCDEdit is a command-line tool for managing BCD stores. It can be used for
a variety of purposes, including creating new stores, modifying existing stores, adding boot menu parameters, and so on. BCDEdit serves essentially the same purpose as Bootcfg.exe on earlier versions of Windows, but with two major
improvements
QUESTION 10
Your company has a single Active Directory Domain Services (AD DS) domain and 1,000 Windows 7 computers. You are planning to deploy a custom application. You need to schedule the deployment to occur outside of business hours and
without user interaction.
What should you do? (Choose all that apply.)
A. Create a collection with the required computers and assign the software to the collection.
B. Create a software installation Group Policy object (GPO).
C. Assign the policy to the root of the Active Directory Domain Services (AD DS) domain.
D. Create a software deployment package by using System Center Configuration Manager 2007.
E. Create an unattend.xml file.
F. Create a silent install MSI file.
Correct Answer: ADF
Explanation
Explanation/Reference:
hints: without user interaction = silent install MSI file
QUESTION 11
A network consists of 1,000 laptop computers that run Windows XP. The computers do not have access to the corporate network.
You plan to migrate 200 of the computers immediately to Windows 7. The remainder will be migrated over the next several months.
You need to plan the most efficient method for activating all of the computers.
What should you do?
A. Use Multiple Activation Key (MAK) Independent for the first 200 computers, and then use Multiple Activation Key (MAK) Proxy for the remaining computers.
B. Use the Key Management Service (KMS) for all the computers.
C. Use Multiple Activation Key (MAK) Independent for all the computers.
D. Use Multiple Activation Key (MAK) Proxy for the first 200 computers, and then use the Key Management Service (KMS) for the remaining computers.
Correct Answer: B
Explanation
Explanation/Reference:
Key Management Service (KMS) requires a count of 25 or higher from the KMS host to activate itself.refer to http://technet.microsoft.com/en-us/library/ee939272.aspx MAK:
If users install a MAK using the user interface (UI), the MAK client attempts to activate itself over the Internet one time. If the users install a MAK using the Slmgr.vbs script, the MAK client does not try to activate itself automatically. refer to
http://technet.microsoft.com/en-us/library/ff793438.aspx Hints:
The computers do not have access to the internet
QUESTION 12
Your company’s network is shown in the following diagram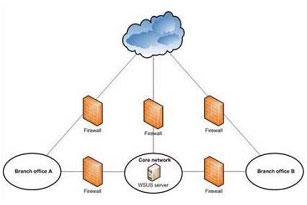
Each office is connected to the Internet through a high-bandwidth connection. The branch offices are connected to the core network through low-bandwidth connections. Microsoft Windows Server Update Services (WSUS) must provide software updates for all offices. You need to design the WSUS infrastructure to minimize traffic over the low-bandwidth connections. Which two actions should you perform? (Each correct answer presents part of the solution. Choose two.) A. Deploy BranchCache on the WSUS server and client computers B. Configure WSUS to use updates that are stored locally C. Configure WSUS to use updates that are stored on Microsoft Update D. Deploy Quality of Service (QoS) on the WSUS server and client computers E. Deploy WSUS servers in the branch offices Correct Answer: CE Explanation Explanation/Reference: WSUS update from Microsoft update is faster then core network Deploy WSUS servers in each branch office in order to provide WSUS server for branch client. hints: 1. Each office is connected to the Internet through a high-bandwidth connection. 2. The branch offices are connected to the core network through low-bandwidth connections.
QUESTION 13
Your network is configured as shown in the following diagram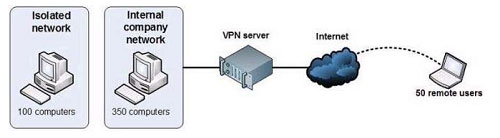 You are planning to deploy Windows 7. You have the following requirements: ?Use BitLocker on all computers in the isolated network. ?Provide DirectAccess on all portable computers. ?Use the Key Management Service (KMS) to activate all client computers. You need to plan a client computer licensing strategy that meets the requirements. What should you do? A. License 500 copies of Windows 7 Ultimate. B. License 500 copies of Windows 7 Enterprise. C. License 350 copies of Windows 7 Professional, license 150 copies of Windows 7 Ultimate, and purchase Software Assurance for the Windows 7 Professional licenses. D. License 350 copies of Windows 7 Enterprise, and license 150 copies of Windows 7 Ultimate. Correct Answer: B Explanation Explanation/Reference: hints: Direct Access only available for Ultimate and Enterprise only. Company should use Enterprise version
You are planning to deploy Windows 7. You have the following requirements: ?Use BitLocker on all computers in the isolated network. ?Provide DirectAccess on all portable computers. ?Use the Key Management Service (KMS) to activate all client computers. You need to plan a client computer licensing strategy that meets the requirements. What should you do? A. License 500 copies of Windows 7 Ultimate. B. License 500 copies of Windows 7 Enterprise. C. License 350 copies of Windows 7 Professional, license 150 copies of Windows 7 Ultimate, and purchase Software Assurance for the Windows 7 Professional licenses. D. License 350 copies of Windows 7 Enterprise, and license 150 copies of Windows 7 Ultimate. Correct Answer: B Explanation Explanation/Reference: hints: Direct Access only available for Ultimate and Enterprise only. Company should use Enterprise version
QUESTION 14
Your company has 1,000 client computers that run Windows 7. The company uses several custom line-of-business applications that are not compatible with Windows 7.
You need to distribute a Microsoft Enterprise Desktop Virtualization (MED-V) virtual machine (VM) image that includes the custom applications to all Windows 7 client computers.
What should you do?
A. Mount the VM image from the MED-V workspace.
B. Deploy the VM image from the MED-V server.
C. Deploy the VM image by using Windows Deployment Services (WDS).
D. Deploy the VM image by using Windows Server Update Services (WSUS).
Correct Answer: B
Explanation
QUESTION 15
Your company plans to upgrade all client computers to Windows 7.
The company uses a custom line-of-business application. The application contains sensitive data. The application will not run on Windows 7
You establish that Microsoft Enterprise Desktop Virtualization (MED-V) is the appropriate technology to allow your organization to continue to use the application.
You need to ensure that the virtual machine (VM) images that contain sensitive data can be used only when the user is connected to the MED-V server.
What should you do?
A. Using MED-V TrimTransfer technology, deploy the VM image over the network
B. In the MED-V console, configure the MED-V workspace to prevent offline operation
C. Use BitLocker Drive Encryption to encrypt the drive on which the VM image is stored
D. Using Microsoft System Center Configuration Manager, deploy the VM image to an image store directory
Correct Answer: B
Explanation
QUESTION 16
The client computers in your network run either Windows XP or Windows 7. All client computers are in a single Active Directory Domain Services (AD DS) organizational unit (OU) named MyClients.You install Windows Software Update Services (WSUS). You create a Group Policy object (GPO) that enables automatic updates from the WSUS server, and you link the GPO to the MyClients OU. You place all client computers in a targeting
group named MyClients.
Testing reveals that a security update that is applicable to both Windows XP and Windows 7 causes a line-of-business application to fail on the Windows XP client computers.
You need to ensure that the application runs on the Windows XP client computers and that the Windows 7 client computers receive the security update.
What should you do?
A. Remove the Windows XP client computers from the MyClients targeting group. Approve the update for installation to the All Computers targeting group.
B. Remove the Windows 7 client computers from the MyClients targeting group. Approve the update for installation to the All Computers targeting group.
C. Create a targeting group named MyXPClients beneath the MyClients targeting group.
Move the Windows XP client computers to the MyXpClients targeting group. Approve the update for installation to the MyClients targeting group.
D. Remove the Windows 7 client computers from the MyClients targeting group. Approve the update for installation to the Unassigned Computers targeting group.
Correct Answer: D
Explanation
Explanation/Reference:
All computers targeting group = assigned group and unassigned group. Unassigned computer targeting group = all computer which is not assign to any group
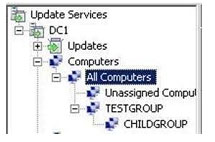
untitled hints: Windows 7 remove from MyClients = unassigned computer targeting group Windows XP = MyClients targeting group update will only done for unassigned computer targeting group
QUESTION 17
Your company uses Microsoft Windows Server Update Services (WSUS) to deploy software updates and service packs. Microsoft releases a security update for Windows 7. You have the following requirements: The security update must be
deployed by 5:00 P.M. on Friday. Computers that are off when the security update is deployed must install the security update as soon as they are turned on. You need to manage the software update process to meet the requirements. What
should you do?
A. Approve the security update for installation through the WSUS console with no deadline.
B. Approve the security update for download through the WSUS console with a deadline of Friday at 5:00 P.M.
C. Approve the security update for installation through the WSUS console with a deadline of Friday at 5:00 P.M.
D. Approve the security update for download through the WSUS console with no deadline.
Correct Answer: C
Explanation
Explanation/Reference:
Hints:
1. question mention at friday 5pm
2. question request install update in stead of download update
QUESTION 18
Your company has a single Active Directory Domain Services (AD DS) domain named contoso.com that uses Active DirectoryCintegrated DNS.
You deploy the Key Management Service (KMS) on a Windows 7 computer.
You need to ensure that Windows 7 client computers can locate the KMS host and perform activation.
Which two actions should you perform? (Each correct answer presents part of the solution.
Choose two.)
A. Create and deploy a GPO firewall rule to allow RPC traffic through TCP port 1688 on the client computers.
B. Deploy a Windows Server 2008 KMS host.
C. Grant the KMS server the Full Control permission on the _vlmcs._tcp.contoso.com DNS record.
D. Grant the KMS server the Full Control permission on the _msdcs._tcp.contoso.com DNS zone.
Correct Answer: AC
Explanation
Explanation/Reference:
http://technet.microsoft.com/en-us/library/ee939272.aspx The KMS clients find the KMS host via a DNS SRV record (_vlmcs._tcp) and then automatically attempt to discover and use this service to activate themselves. When in the 30 day Out
of Box grace period, they will try to activate every 2 hours. Once activated, the KMS clients will attempt a renewal every 7days.
Listening on Port:
Communication with KMS is via anonymous RPC. 1688 is the default TCP port used by the clients to connect to the KMS host. Make sure this port is open between your KMS clients and the KMS host.
QUESTION 19
Your network contains 5 servers that have the Remote Desktop Session Host role service installed. The servers host a Remote Desktop RemoteApp named App1.
You need to recommend a solution for App1 that meets the following requirements:
?Must ensure that users can connect to any Remote Desktop Session Host server
?Must ensure that users are automatically reconnected to disconnected sessions
What should you include in the recommendations?
A. Windows Virtual PC and Windows XP Mode
B. Remote Desktop Web Access
C. Remote Desktop Gateway
D. Windows Deployment Services
E. Remote Desktop Connection Broker
Correct Answer: E
Explanation
Explanation/Reference:
Remote Desktop Connection Broker (RD Connection Broker), formerly Terminal Services Session Broker (TS Session Broker), is used to provide users with access to RemoteApp and Desktop Connection. RemoteApp and Desktop
Connection provides users a single, personalized, and aggregated view of RemoteApp programs, session-based desktops, and virtual desktops to users. RD Connection Broker supports load balancing and reconnection to existing sessions
on virtual desktops, Remote Desktop sessions, and RemoteApp programs accessed by using RemoteApp and Desktop Connection. RD Connection Broker also aggregates RemoteApp sources from multiple Remote Desktop Session Host
(RD Session Host) servers that may host different RemoteApp programs. http://technet.microsoft.com/en-us/library/dd560675(v=WS.10).aspx
QUESTION 20
Your company has two network segments. The core network segment is where centralized management is performed. The high-security network segment is an isolated network. A firewall between the core network segment and the high-
security network segment limits network communication between the segments.
These network segments are shown in the following diagram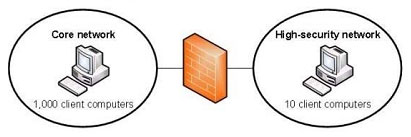
Your company plans to deploy Windows 7 to all client computers.
You need to manage activation for client computers that are located in the high-security network segment.
What should you do?A. Deploy the Key Management Service (KMS) in the core network segment.
B. Deploy the Key Management Service (KMS) in the high-security network segment.
C. Install the Volume Activation Management Tool (VAMT) in the core network segment.
D. Install the Volume Activation Management Tool (VAMT) in the high-security network segment.
Correct Answer: D
Explanation
Explanation/Reference:
Key Management Service (KMS) requires a count of 25 or higher from the KMS host to activate itself.
refer to http://technet.microsoft.com/en-us/library/ee939272.aspx There is a firewall blocking, (VAMT) should setup at high-security network.
QUESTION 21
Your company has client computers that run Windows XP Professional.
You are planning to install Windows 7 Enterprise on the existing client computers.
You need to ensure that the user state can be viewed after it has been collected and saved.
What are two possible ways to achieve this goal? (Each correct answer presents a complete solution. Choose two.)
A. Perform an offline migration by using Windows PE.
B. Use an uncompressed migration store.
C. Perform an offline migration by using Windows.old.
D. Use a hard-link migration store.
Correct Answer: BD
Explanation
QUESTION 22
A company runs Windows Server 2008 R2 in an Active Directory Domain Services (AD DS) environment. Windows 7 is installed on all the companys client computers.
You add a domain user account named User1 to the local Administrators group on a client computer named PC01. When User1 returns to the office, User1 does not have administrative access on PC01.
When you inspect PC01, you find that the local Administrators group does not contain the user account. You need to ensure that User1 is a member of the local Administrators group.
Which Group Policy setting should you select? To answer, select the appropriate Group Policy setting in the work area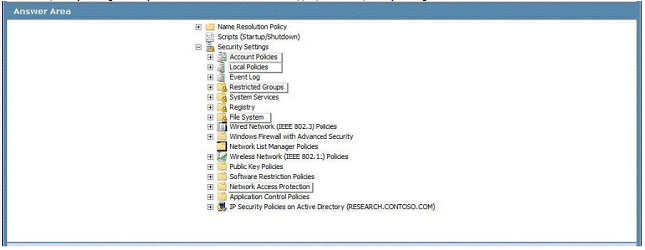
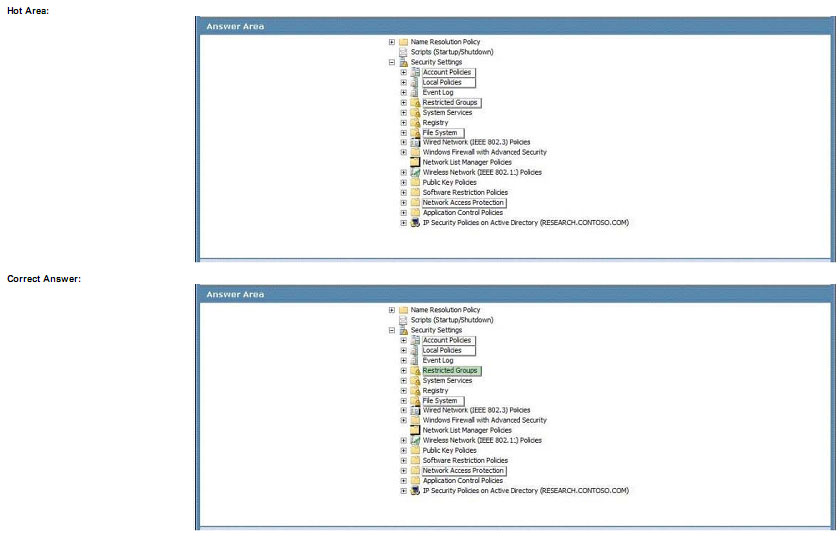
Explanation
Explanation/Reference:
QUESTION 23
You are designing a Windows 7 deployment image.
You plan to install Windows 7 Enterprise with a Multiple Activation Key (MAK).
You need to add the MAK to the configuration pass by using an answer file.
To which configuration pass should you add the MAK?
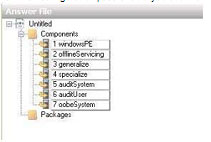

Explanation
Explanation/Reference:
QUESTION 24
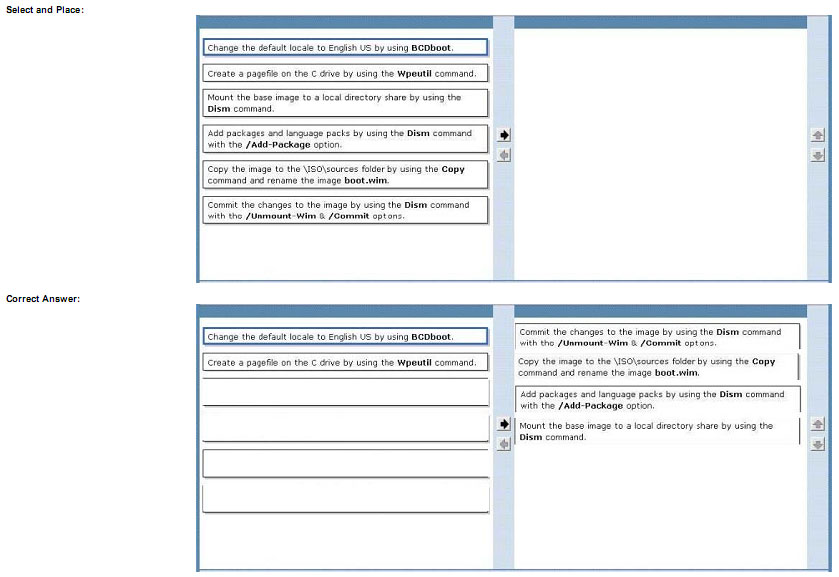
You are the desktop architect for an enterprise organization with computers that run Windows 7 Enterprise.
You need to create a customized WinPE image.
Which four actions should you perform in sequence? (To answer, move the appropriateactions from the list of actions to the answer area and arrange them in the correct order,) 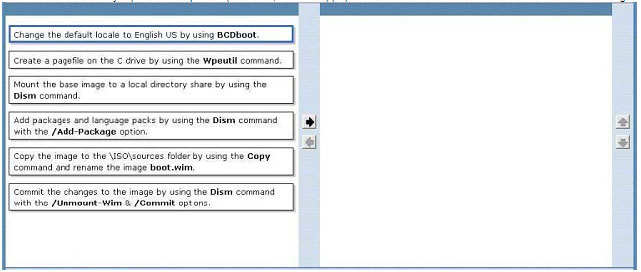
Explanation
Explanation/Reference:
QUESTION 25
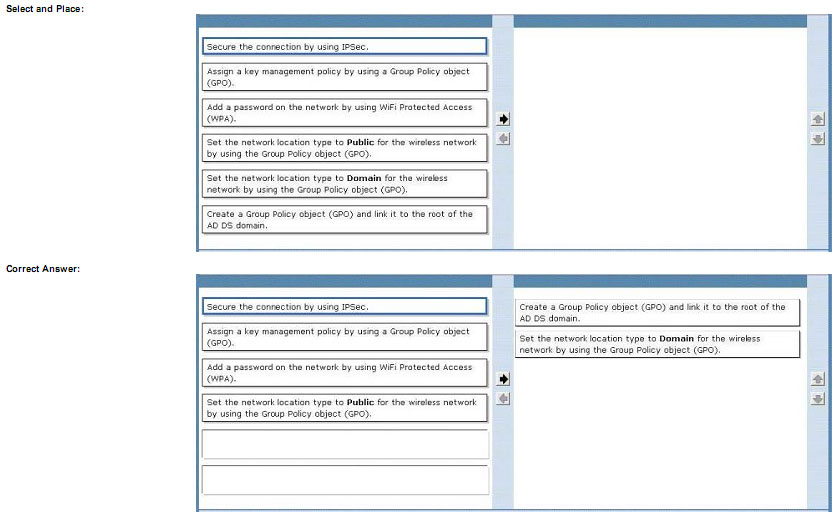
A company has client computers in an Active Directory Domain Services (AD DS) environment. You deploy a new wireless access point (WAP). Third-party security software
controls access to the wireless network.
Users are able to connect to the wireless network and access the Internet but are unable to access the company’s file servers.
You need to enable users to connect to the file servers by using the wireless network.
Which two actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)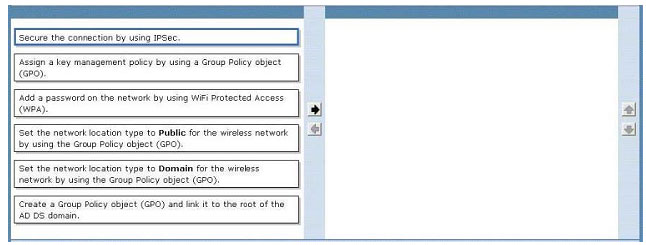
Explanation
Explanation/Reference:
QUESTION 26
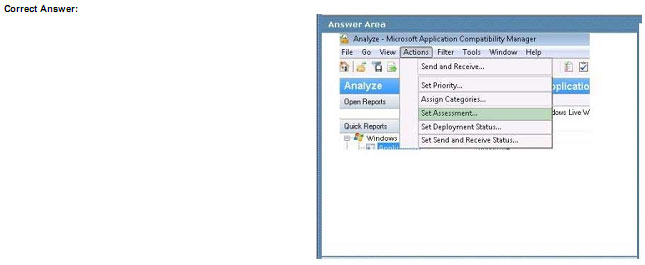
You use Microsoft Application Compatibility Manager to produce a report that lists a company’s applications and their compatibility status with Windows 7.
You need to add your ratings of the compatibility of the applications to the report.
Which Microsoft Application Compatibility Manager action should you select? To answer, select the appropriate setting or settings in the work area.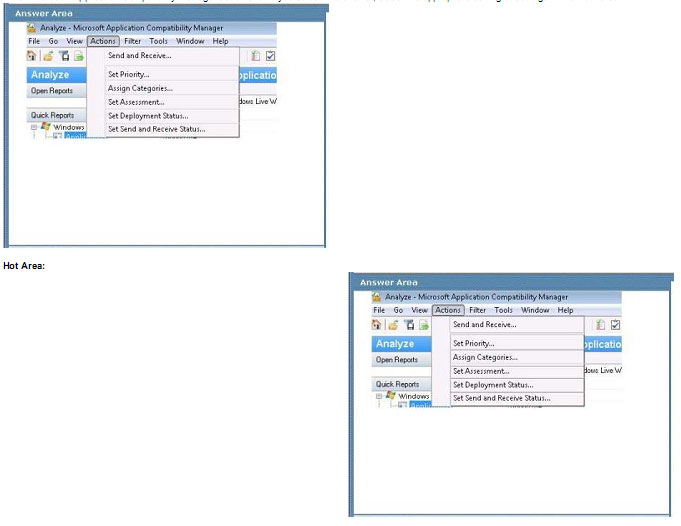
Explanation
Explanation/Reference:
QUESTION 27
All client computers in a company run Windows 7 Enterprise. The company creates Windows PowerShell scripts to collect statistical data from client computers. A logon script is configured to run the PowerShell scripts during logon.
An error occurs when the scripts are run on client computers.
You need to ensure that all PowerShell scripts run correctly.
Which command should you use? (To answer, drag the appropriate component from the list of components to the correct location or locations in the work area.)
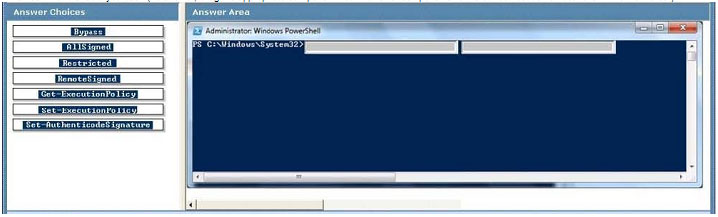
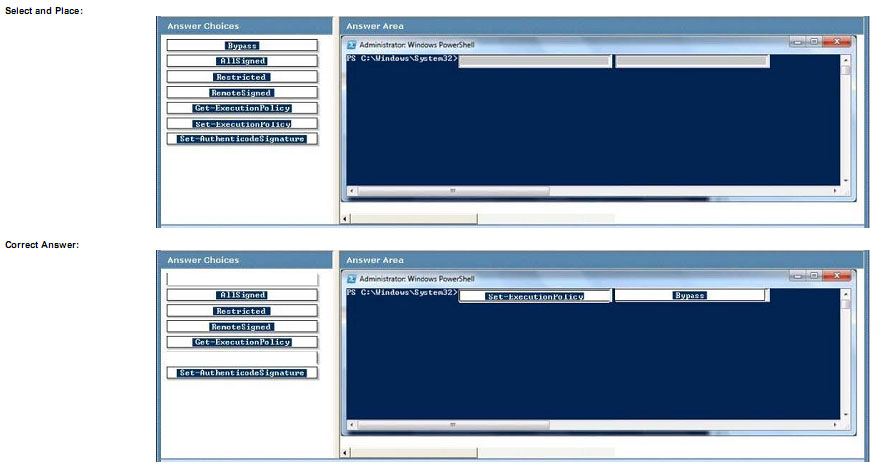
Explanation
Explanation/Reference:
QUESTION 28
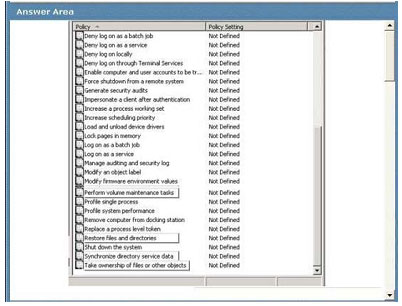
A company runs Windows Server 2008 R2 in an Active Directory Domain Services (AD DS) environment. Windows 7 is installed on all client computers.
Users discover that they cannot delete files that they have created and placed in their local folders.
You need to enable users to modify file permissions.
Which setting should you configure? To answer, select the appropriate setting or settings in the work area
Explanation
Explanation/Reference:
QUESTION 29
A company’s server runs Windows 2008 R2 with Active Directory Domain Services (AD DS) and Windows Server Update Services (WSUS). All client computers run Windows 7 Enterprise.
You need to automate the distribution of Windows security updates to all client computers by meeting the following requirements:
1) Point all client computers to the WSUS server.
2) Schedule updates to install at a specific time.
3) Run the updates immediately after Windows starts if the computer missed the originally scheduled updates.
You need to configure Group Policy to meet the requirements.
Which settings should you configure? To answer, select the appropriate setting or settings in the work area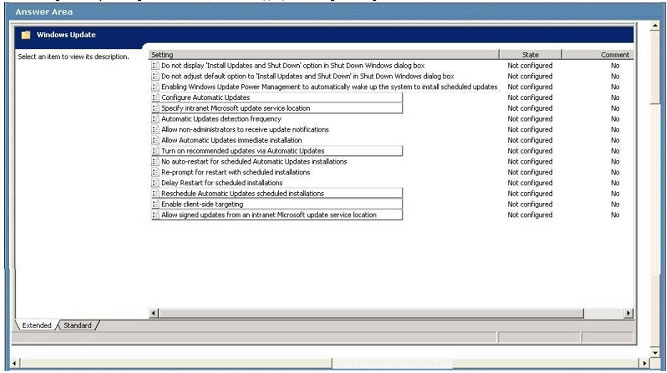
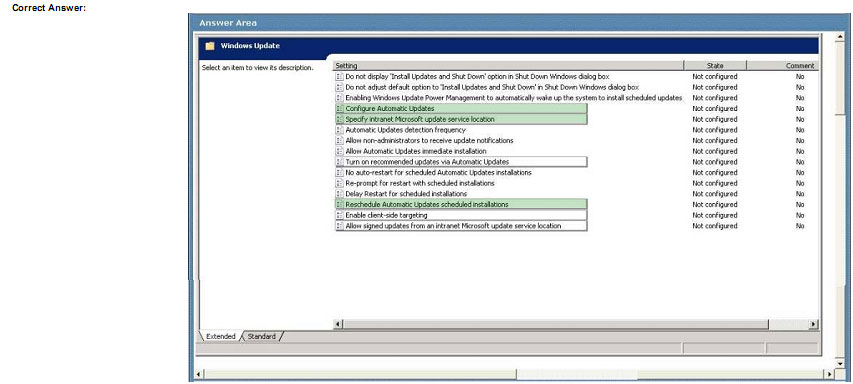
Explanation
Explanation/Reference:
QUESTION 30
You use Group Policy to configure Windows 7 Enterprise client computers.
You need to modify a Group Policy object (GPO) to specify a custom location for the temp folder.
Which setting should you select? To answer, select the appropriate setting or settings in the work area.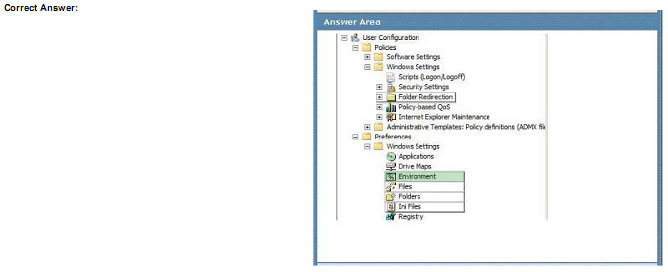
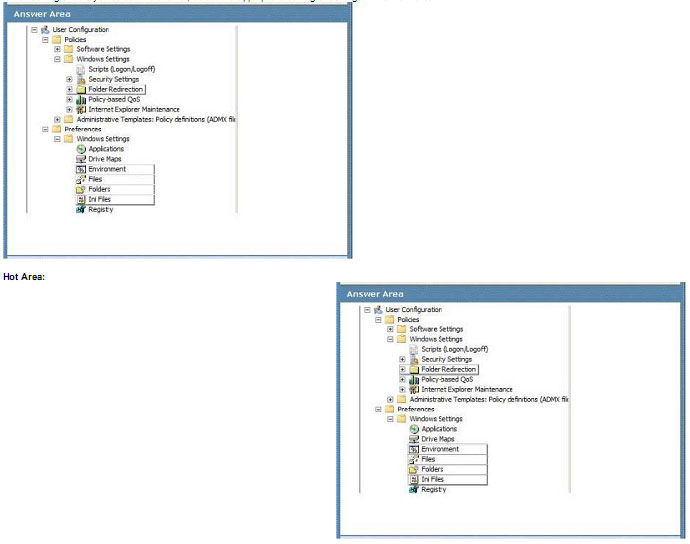
Explanation
Explanation/Reference:
QUESTION 31
A company has client computers that run windows 7. A new corporate security policy states that all client computers in the legal department should allow only inbound and outbound network connections for which there is an existing firewall
rule.
You need to ensure that all client computers in the legal department are configured to follow the new security policy.
Which settings should you select? To answer, select the appropriate setting or settings in the work area
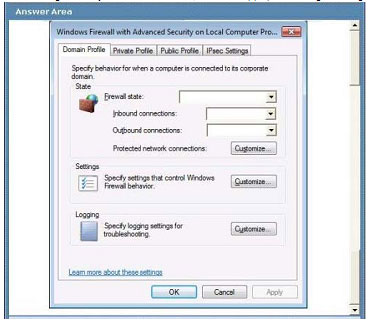
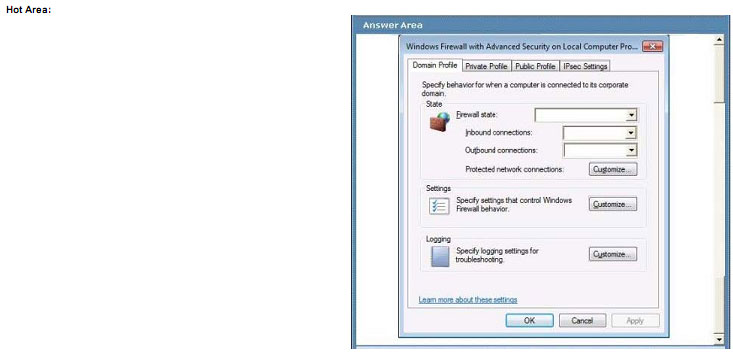
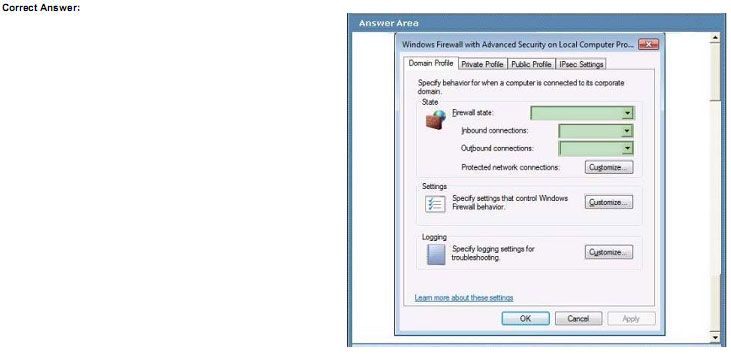
Explanation
Explanation/Reference:
QUESTION 32
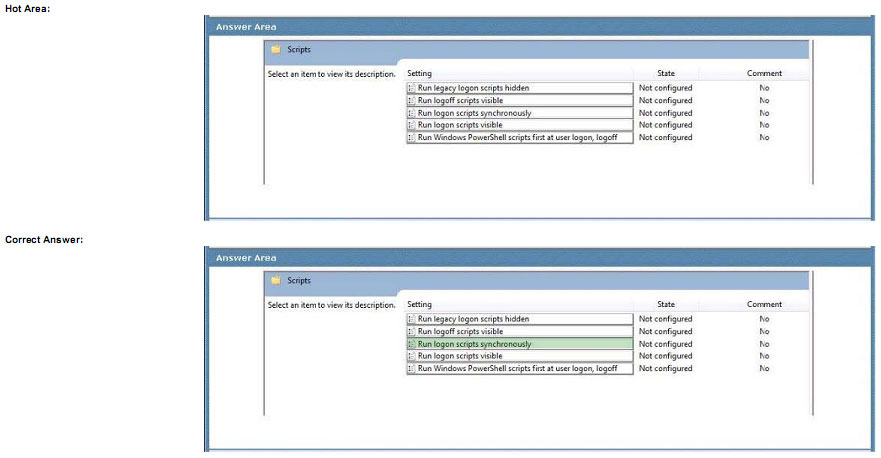
You are the desktop architect for an enterprise organization with computers that run Windows 7.
You need to create a Group Policy object (GPO) to prevent Windows Explorer from starting until all logon scripts have finished.
Which setting should you select? To answer, select the appropriate setting in the work area.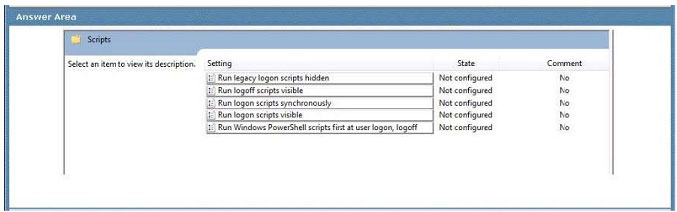
Explanation
Explanation/Reference:
QUESTION 33
You are designing a Windows 7 image creation strategy for a multilingual deployment. You currently have an English language image of Windows 7.
The deployment must meet the following requirements:
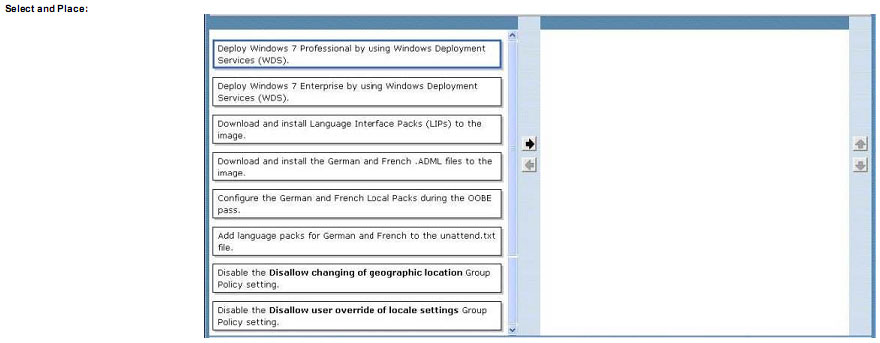
You need to recommend an action plan that meets the deployment requirements.
Which two actions should be performed in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.)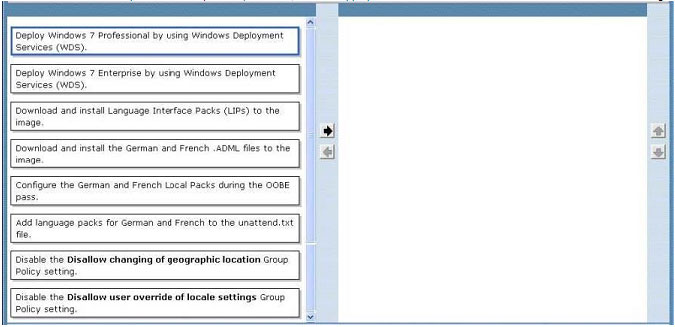
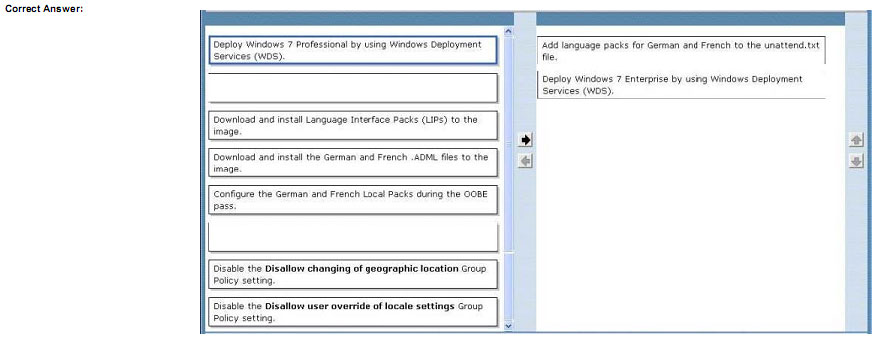
Explanation
Explanation/Reference:
QUESTION 34
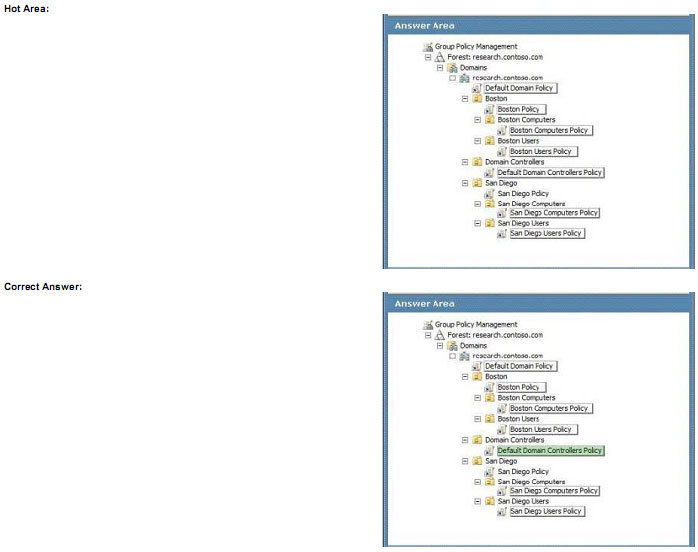
Active Directory Domain Services (AD OS) is running on windows Server 2008 R2.
You decide to audit changes to AD DS.
Administrative users in San Diego add new users to the domain without approval. You configure the audit policy settings in the San Diego Policy Group Policy object (GPO) and set up auditing in object System Access Control Lists, YOU
verify that the GPO is being applied to the resources in the San Diego OUs, but auditing still does not work.
You need to select the GPO to ensure that users added by the San Diego administrative users are audited.
Which GPO should you select? To answer, select the appropriate setting or settings in the work area.
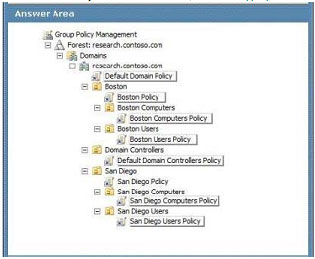
Explanation
Explanation/Reference:
QUESTION 35
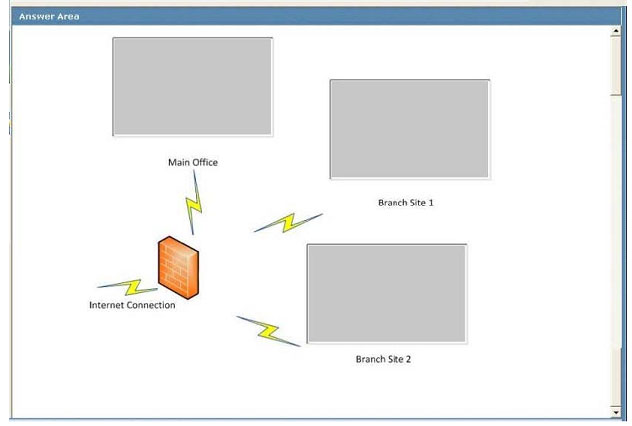
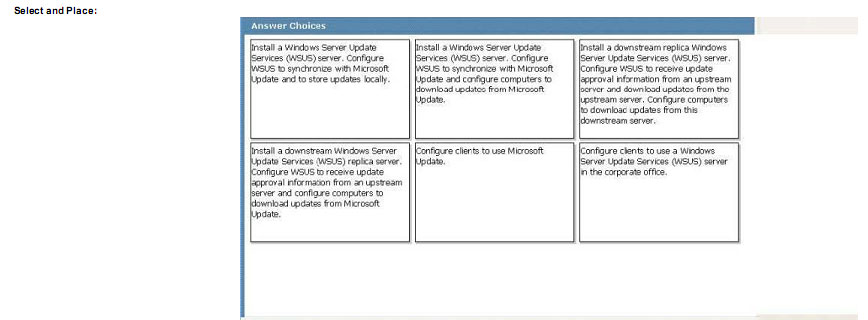
A company has a main office and two branch offices named Branch Site 1 and Branch Site 2. The main office has a server that runs Windows Server 2008 R2. Branch Site 2 also has a server that runs Windows Server 2008 R2. The branch
offices do not have direct access to the Internet.
Windows 7 Enterprise is installed on all client computers. A diagram of the network is shown in the exhibit.
Corporate policy dictates that all updates must be approved by the IT department before being deployed.
Using the hardware configuration shown in the exhibit, you need to design a Windows Update strategy to meet the following goals:
What should you recommend? (To answer, drag the appropriate answer to the correct location or locations in the work area.)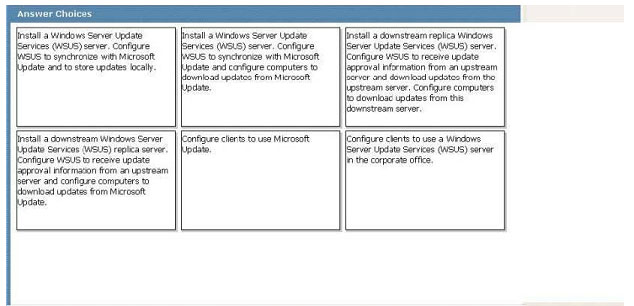
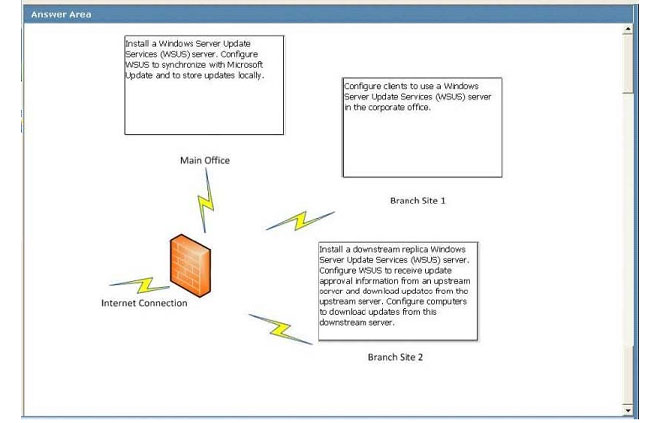
Explanation
Explanation/Reference:
QUESTION 36
A server runs Windows Server 2008 P2 with Remote Desktop Services (RDS).
You add an application to Remote Desktop RemoteApp.
You need to ensure that the application can be published by using Group Policy.
Which setting should you select? To answer, select the appropriate setting or settings in the work area.
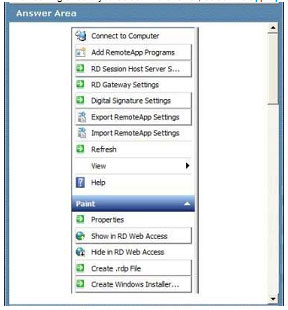
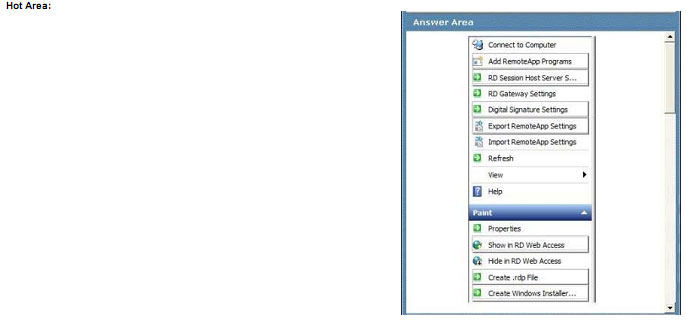
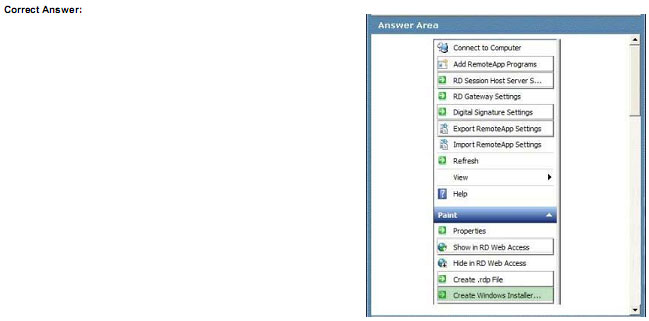
Explanation
Explanation/Reference:
QUESTION 37
You are designing a Windows 7 Enterprise custom image. You create an autounattend.xml file by using Windows System Image Manager (SIM). This file will be used when the image is deployed.
You are planning to install Windows 7 on a second hard disk in a computer. You configure the DiskID setting.
You need to select the configuration pass where you will add the DiskID setting.
Which option should you select? To answer, select the appropriate setting or settings in the work area.
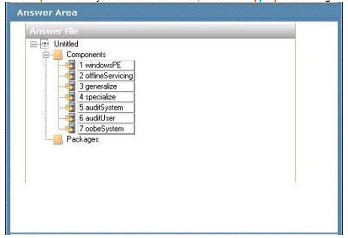
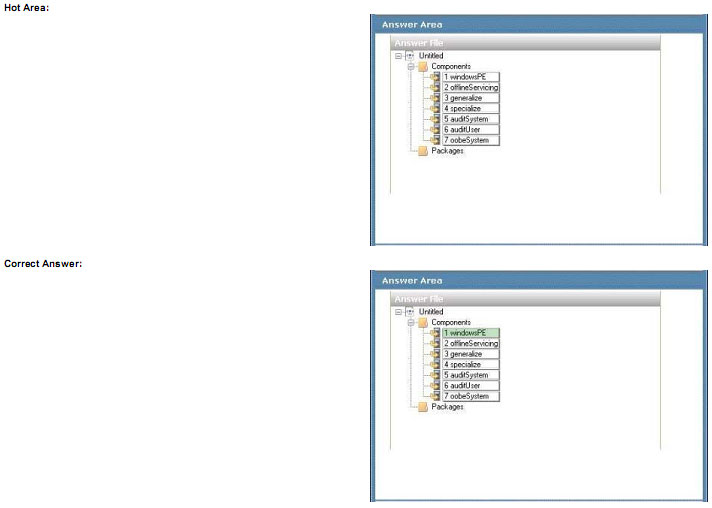
Explanation
Explanation/Reference:
QUESTION 38
A company has a server that runs Windows Server 2008 R2 in an Active Directory Domain Services (AD DS) environment. The domain controllers were recently upgraded from Windows Server 2003. You are using Group Policy to deploy
applications to the client computers remotely. The computers reboot each night as part of routine maintenance.
You need to ensure that the application installs when the computer starts up.
Which Group Policy setting should you configure? To answer, select the appropriate setting or settings in the work area.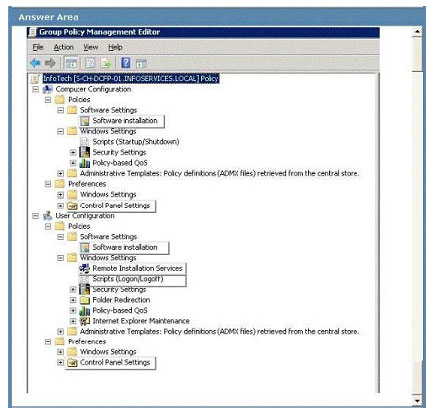
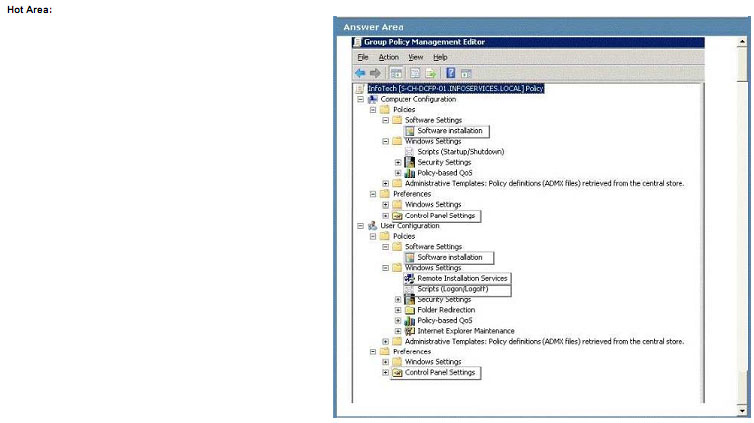
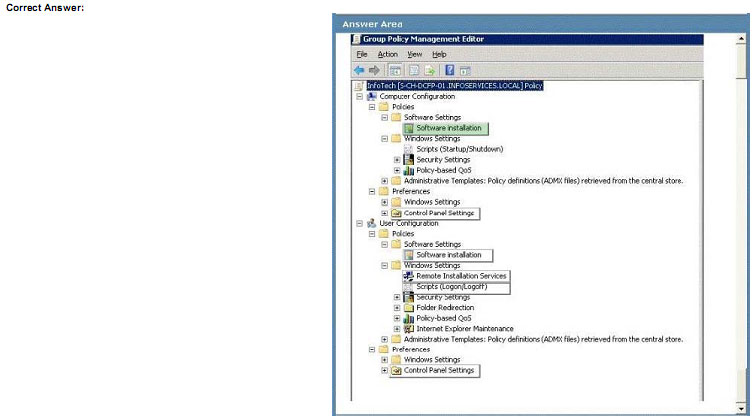
Explanation
Explanation/Reference:
QUESTION 39
All portable computers on a company’s wireless network run windows 7 Enterprise.
You need to ensure that users can connect only to the predefined SSID shown in the work area.
Which Group Policy object (GPO) settings should you select? To answer, select the appropriate setting or settings in the work area.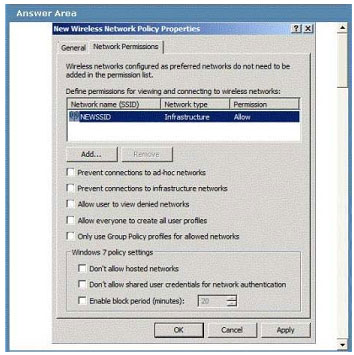
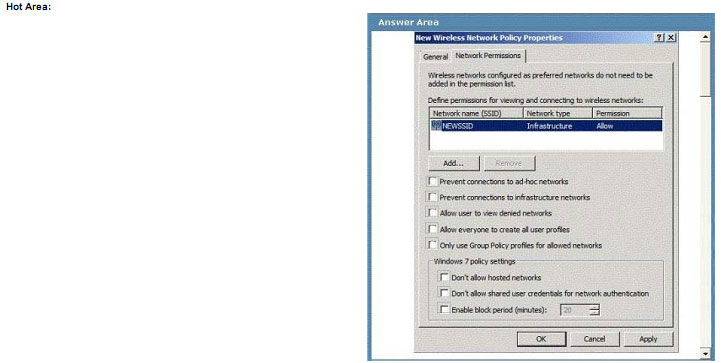
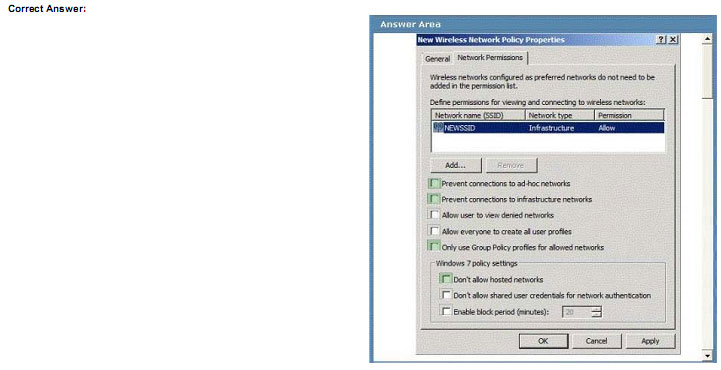
Explanation
Explanation/Reference:
QUESTION 40
You are managing data migration from an existing Windows 7 computer to a new Windows 7 computer. You need to migrate user and application data from the existing computer to the new computer.
Which command should you run on the existing and new computers? (To answer, drag the appropriate commands to the correct location in the work area.)
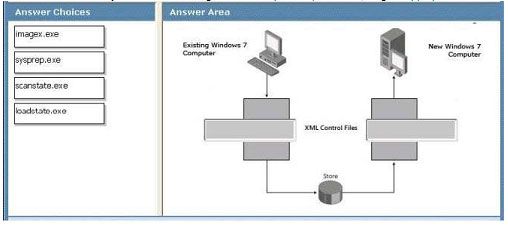
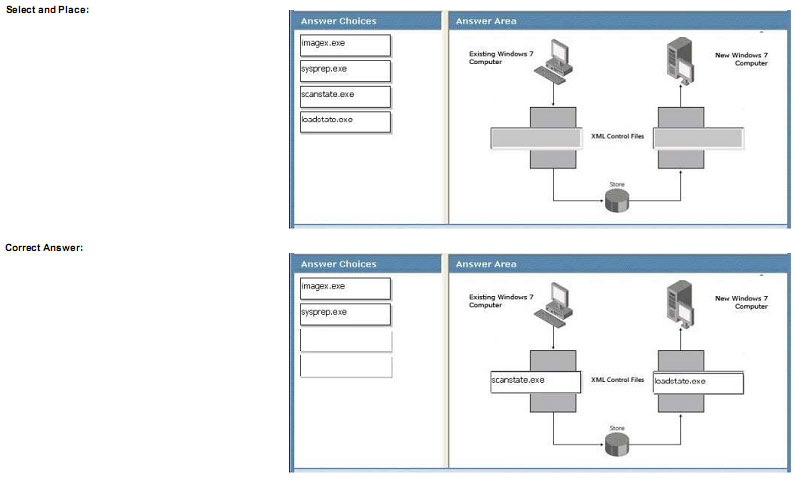
Explanation
Explanation/Reference:
QUESTION 41
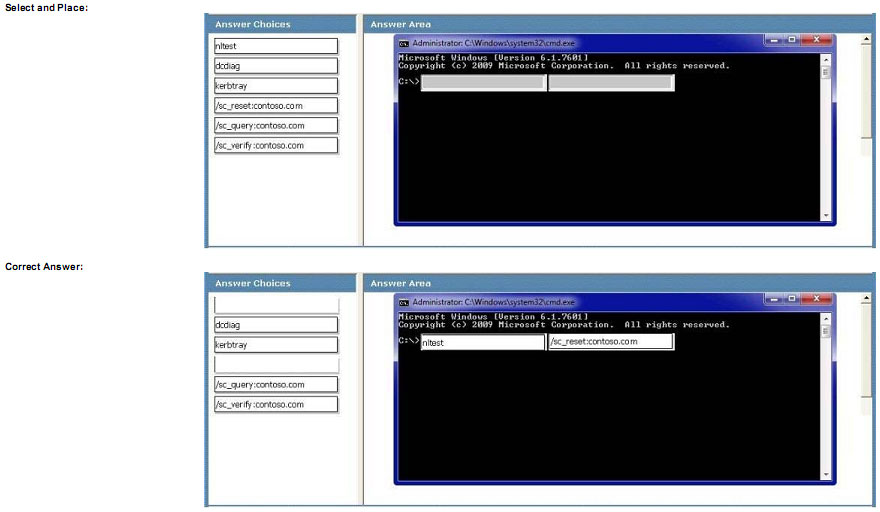
An enterprise organization has computers that run Windows 7. Users log on to the Contoso.com domain from their client computers.
A user is unable to log on to the domain. The user changed his password the previous night and was unable to log on this morning. After reviewing the event logs, you notice a large amount of NETLOGON errors.
You need to ensure that the user can log on to the domain.
Which command should you run? (To answer, drag the appropriate command and parameter from the list of commands and parameters to the correct location or locations in the work area.)
Explanation
Explanation/Reference:
QUESTION 42
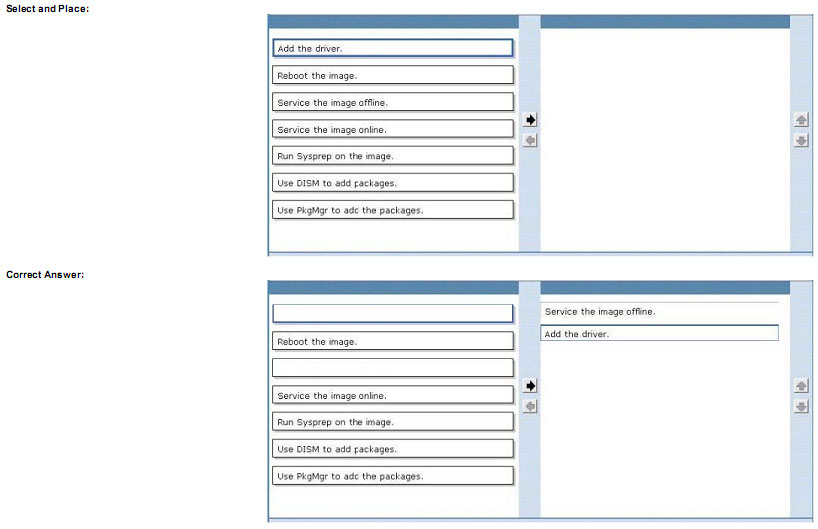
You are updating the corporate image to add drivers to support a new device.
You need to meet company requirements for updating images.
Which two actions should you perform in sequence? (To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.
Explanation
Explanation/Reference:
Conclusion:
Work2You free sharing of 42 Microsoft PRO 70-686 Exam dumps to help you open the door to learning, really want to pass the exam you need to choose the full 70-686 exam dump, all of our exam content from Pass4itsure, if you want to easily get 70-686 exam certification, please choose Select https://www.pass4itsure.com/70-686.html (Q&As:184 latest update).
[PDF] Free Microsoft PRO 70-686 dumps download from Google Drive: https://drive.google.com/open?id=1AnRkEHVsAqaY174JMIe0kqBCLo-R6A3-
[PDF] Free Full Microsoft dumps download from Google Drive: https://drive.google.com/open?id=1gdQrKIsiLyDEsZ24FxsyukNPYmpSUDDO
pass4itsure 15% OFF Coupon code
related: https://www.work2you.org/the-prospect-of-msce-certification-training/